Looking at IEC 61850, Part 4: The Cybersecurity Impact
During an open forum at a recent seminar for professionals in the field of protection & control (P&C), the moderator prodded attendees – technicians, engineers, system administrators – with probing questions: What are your struggles? What do you need? How can we help you? A wireless microphone buried in a plush cube was literally tossed around so those with something to say skillfully played catch with each other across the ballroom. IEC 61850 was the subject that got the most comments.
Some said it’s not something they’re considering; others said they’re looking at it; others shared some lessons learned from implementing it. Cybersecurity was the topic I listened for in that discussion.
Protecting Protection & Control
Utilities fight back hundreds of thousands of cyberattacks every month. Cyber defenses aren’t cheap and neither are NERC CIP penalties (here in North America) on top of recovery expenses if something gets missed. Substation automation definitely gets the attention of industry regulators and owner-operators since it involves networks of computer equipment involved in the protection and control of power systems. Obviously, these networks must be protected for the sake of system reliability. Industry players have tremendous incentives to prioritize cybersecurity throughout substation networks anyway, but especially those at facilities operating at voltage levels that support bulk electric power delivery.
Many Eggs in One Basket
Substation automation is coordinated integration — multiple discrete functions happening as integrated processes. In the context of P&C, microprocessor-based (MP) relays enable automation. As programmable electronic devices, MP relays use an algorithmic paradigm for tripping built upon logical (if, and, or) expressions that give protection engineers many possible ways to design advanced schemes. Ultimately, the intricacies of their schemes become settings in the programming of the relays. Tripping parameters of protection elements become set like so many other functions – monitoring, alarming, event capture, self-checking – all coordinated and governed by logic.
MP relays receive wired inputs from instrument transformers and use wired inputs and outputs to control circuit breaker operations in their given protection schemes. Other connections (for Ethernet over copper/Ethernet over fiber) join them to networks of equipment in communication schemes that coordinate relays device-to-device using protocols that invoke redundancy among segments of the power system if local protection fails. Device-level communication schemes, such as those for P&C, contribute vital information to SCADA aggregations at the station level.
Automation rests on the capabilities of multi-function MP relays, but one significant problem complicates the whole matter: the marketplace. Manufacturers of MP relays compete on features at least as much as prices and support offerings. Customer by customer, features required within bid specs extend what manufacturers produce, resulting in huge amounts of capabilities being amassed along with heaps of setup choices. Such gigantic feature sets increase the complexity of engineering, commissioning, and maintenance especially with relays from different manufacturers that have their own ins-and-outs regarding settings, logic, and communications.
Enter IEC 61850
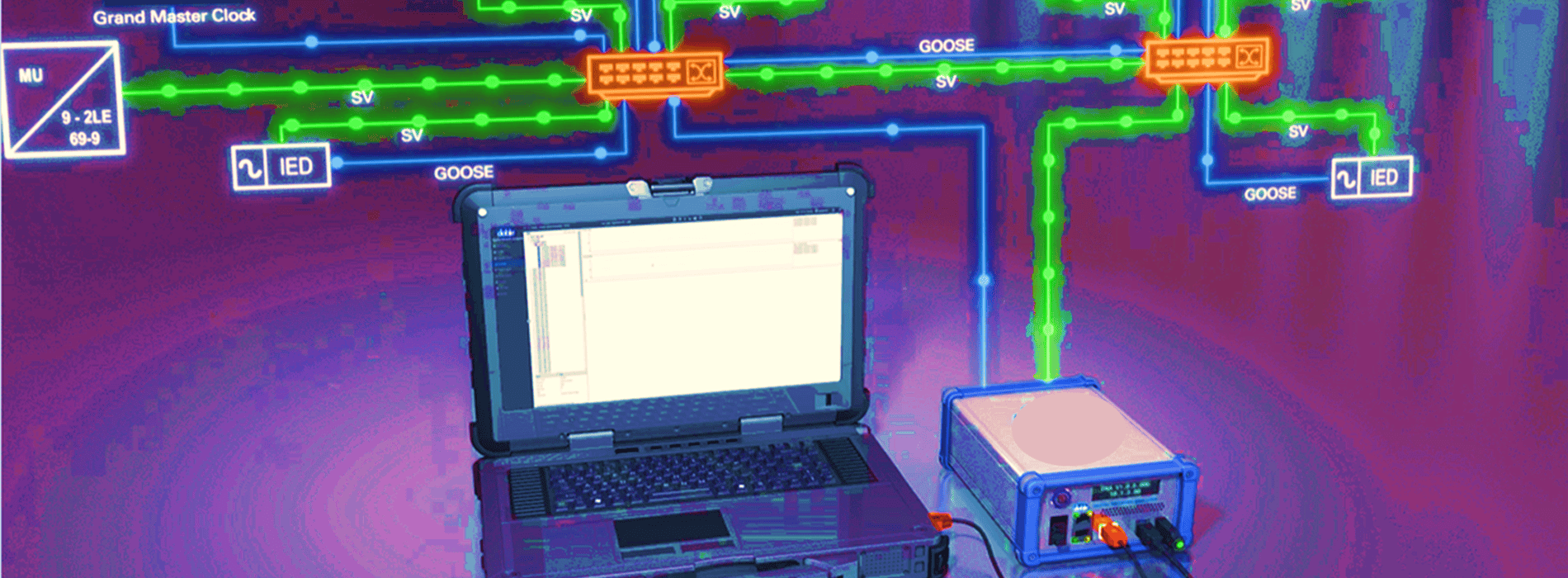
IEC 61850 and its associated standards define protocols that manufacturers can implement to overcome proprietary differences that generally impede device-to-device communications between commercially diverse relays. Interoperability is great, but the catch is automation schemes based on IEC 61850 exist digitally in substation LAN/WAN topologies…gone are the wires (replaced by Ethernet cables) but not the complexity. MP relays that can support Ethernet-based, digital schemes like ones based on IEC 61850 are considered intelligent electronic devices, so-called IEDs.
IEC 61850-based P&C invokes a whole different set of concepts – SV/GOOSE/MMS, publishing/subscribing, test/simulate modes, mapping logic to digital I/O of IEDs, to name a few – that change the game on engineers and technicians. Their functional areas enter the domain of network specialists and vice versa when it gets down to actually implementing IEC 61850 in digital substation infrastructures and maintaining automation through IEDs.
Cybersecurity is Paramount
Speaking of infrastructures, critical ones – like high voltage electric systems – are significantly consequential to society which, unfortunately, makes them the targets of cyberattacks. Bad actors are becoming more sophisticated all the time; their techniques are being honed from their ceaseless attempts at disrupting large-scale electric systems by compromising their cyber defenses.
The power Industry has responded with numerous countermeasures – access controls; hardened laptops; multi-factor authentications; password management; segmentation and firewalls; encrypted data in transit; secure communication protocols; regular patching and updates – in defense of its assets and interests. One particular standards series, IEC 62351 for security of control centers and communication networks, lays out methodologies that entities have been adopting for years on this front.
Are security risks higher in IEC 61850 implementations?
Protection, communication, and control inter-dependencies carry the same criticality whether we’re talking about systems that are Ethernet-based and digital or point-to-point and hardwired. For all intents and purposes, cybersecurity is essentially as stringent for one as the other. As far as the industry is concerned, the attack surface calls for a robust cybersecurity posture either way.
Check back for Part 5 in this 5-part series of The Relay™ newsletter where we look at the investment behind a move to IEC 61850.
Additional Information:
- Originally published in the The Relay™ Newsletter. Subscribe on LinkedIn.
- Learn about Doble Protection Testing Solutions
- Looking at IEC 61850, Part 1: The Relay Technician
- Looking at IEC 61850, Part 2: The Protection Engineer
- Looking at IEC 61850, Part 3: The Laboratory